This is the fifth edition of Brainwaves hackathon. The challenges are based on filesystems i.e. how data is stored in the hard disk. We are provided with 2 dumps of a hard disk.
Dump 1
The first sector of the hard disk is been modified. To load the boot loader successfully at every boot process we need to fix it. Your task is to fix the first sector and upload it back to us. Corrupted bytes of the partition entries are replaced with value "CC". So you need to fix these fields only.
According to wiki, the first sector is a special boot sector called master boot record (MBR). After analyzing the given dump using hexl-mode in emacs, I found the corrupted cc bytes.
000001b0: cd10 ac3c 0075 f4c3 608d 3b68 0000 0020 ...<.u..`.;h... 000001c0: 2100 debe 122c 0008 0000 cccc cccc 00be !....,.......... 000001d0: 132c 075d 0459 00f8 0a00 00f0 0a00 005d .,.].Y.........] 000001e0: 0559 07fe ffff cccc cccc 00d0 e31d 00fe .Y.............. 000001f0: ffff 0ffe ffff 00b8 f91d 00a0 3e1c 55aa ............>..U
According to MBR layout, the master partition table start at address 1BE and ends with boot signature 55AA. The partition table consists of 4 entries and each entry looks like:
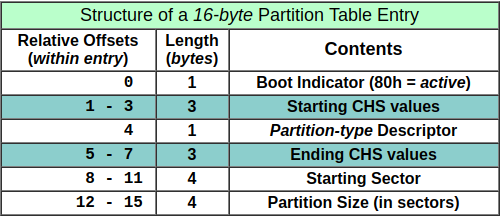 Based on the above information, the 4 partition entries in MBR are (the values have been converted from little-endian to big-endian):
Based on the above information, the 4 partition entries in MBR are (the values have been converted from little-endian to big-endian):
| Boot indicator | CHS(start) | Partition type | CHS(end) | Starting sector | Partition Size |
|---|---|---|---|---|---|
| 00 | 002120 | de | 2c12be | 00000800 | cccccccc |
| 00 | 2c13be | 07 | 59045d | 000af800 | 000af000 |
| 00 | 59055d | 07 | fffffe | cccccccc | 1de3d000 |
| 00 | fffffe | 0f | fffffe | 1df9b800 | 1c3ea000 |
To fix the first 4 corrupted bytes, I need to find the size of first partition which can be calculated as difference of CHS_END and CHS_START. But first the CHS values needs to be decoded and converted in units of sectors. After reading this post, I wrote a script that decode the 3 byte CHS hex value.
inp = 0x5d0559 # 3 byte CHS
head = inp >> 16
sect = (inp & 0x003F00) >> 8
cyn = ((inp & 0x00C000) >> 6) | (inp & 0x0000FF)
print('CHS : ', cyn, head, sect) # CHS: 89, 93, 5The decoded CHS values can be converted into sectors using (CYLINDER*heads_per_cylinder + HEAD )*sectors_per_head + SECTORS but I needed the system constants heads_per_cylinder and sectors_per_head.
To calculate these constants, I used the values of 2nd partition. The first equation came using partition size and second using starting sector(LBA) entry which is equal to CHS_FIRST(in sectors)-1. Solving these 2 equations, we get
heads_per_cylinder = 255 sectors_per_head = 63
Now the size of partition 1 came out 716800 (0x000af000). Similarly I calculated starting sector (LBA) 0x0015e800.
After putting these values in the dump (converted to little-endian in the dump), it looked like
000001b0: cd10 ac3c 0075 f4c3 608d 3b68 0000 0020 ...<.u..`.;h... 000001c0: 2100 debe 122c 0008 0000 00f0 0a00 00be !....,.......... 000001d0: 132c 075d 0459 00f8 0a00 00f0 0a00 005d .,.].Y.........] 000001e0: 0559 07fe ffff 00e8 1500 00d0 e31d 00fe .Y.............. 000001f0: ffff 0ffe ffff 00b8 f91d 00a0 3e1c 55aa ............>.U.
Questions based on dump 1
Q1. How many primary partitions are there in the hard disk dump?
3, the 4th partition is an extended partition because its partition type is 0f and others are primary partitions.
Q2. What is the disk signature of the hard disk for the given dump?
55AA. The last 2 bytes of the first sector.
Q3. How many NTFS partitions are there?
2, partition type of NTFS is 07.
Q4. What is the size of hard disk in MBs?
It can be calculated by adding size of the partitions and multiplying by bytes_per_sector(0x200).
Dump 2
The first sector of 2nd partition is modified to make the partition unusable by the operating system. Your task is to fix the first sector and upload it back to us. MFT table of the partition is at the offset 0x1d3aa000 bytes from starting in the hard disk.
00000000: cc52 904e 5446 cc20 2020 2000 0208 0000 .R.NTF. ..... 00000010: 0000 0000 00f8 0000 3f00 ff00 00f8 0a00 ........?....... 00000020: 0000 0000 8000 8000 cccc cccc cccc cccc ................ 00000030: cccc cccc cccc cccc 0200 0000 0000 0000 .t..............
The first 2 corrupted bytes can be easily fixed if you look at wiki. The next 8 bytes at address 0x28 represents partition size which can looked from the partition size entry corresponding to partition2 in the partition table.
The next 8 bytes represents MFT offset from start of partition. It was calculated as difference of starting byte of 2nd partition (calculated by multiplying starting sector and bytes_per_sector) and given absolute address of MFT which came out to be 0x74aa000 bytes. Now it needed to be converted in units of clusters which was done by dividing bytes_per_sector (0x200) and sectors_per_cluster (0x08). And I went to address 0x74aa000 and found the MFT was there so the calculations were correct.
074aa000: 4649 4c45 3000 0300 2f4c 4000 0000 0000 FILE0.../L@..... 074aa010: 0100 0100 3800 0100 9801 0000 0004 0000 ....8........... 074aa020: 0000 0000 0000 0000 0700 0000 0000 0000 ................ 074aa030: 0300 ffff 0000 0000 1000 0000 6000 0000 ............`... 074aa040: 0000 1800 0000 0000 4800 0000 1800 0000 ........H....... 074aa050: 78af 695d 9cd6 d001 78af 695d 9cd6 d001 x.i]....x.i].... 074aa060: 78af 695d 9cd6 d001 78af 695d 9cd6 d001 x.i]....x.i].... 074aa070: 0600 0000 0000 0000 0000 0000 0000 0000 ................ 074aa080: 0000 0000 0001 0000 0000 0000 0000 0000 ................ 074aa090: 0000 0000 0000 0000 3000 0000 6800 0000 ........0...h... 074aa0a0: 0000 1800 0000 0300 4a00 0000 1800 0100 ........J....... 074aa0b0: 0500 0000 0000 0500 78af 695d 9cd6 d001 ........x.i].... 074aa0c0: 78af 695d 9cd6 d001 78af 695d 9cd6 d001 x.i]....x.i].... 074aa0d0: 78af 695d 9cd6 d001 0040 0000 0000 0000 x.i].....@...... 074aa0e0: 0040 0000 0000 0000 0600 0000 0000 0000 .@.............. 074aa0f0: 0403 2400 5300 4f00 4300 4700 4500 4e00 ..$.S.O.C.G.E.N 074aa100: 8000 0000 4800 0000 0100 4000 0000 0600 ....H.....@..... 074aa110: 0000 0000 0000 0000 3f00 0000 0000 0000 ........?.......
This is how the dump looks after fixing it.
00000000: eb52 904e 5446 5320 2020 2000 0208 0000 .R.NTFS ..... 00000010: 0000 0000 00f8 0000 3f00 ff00 00f8 0a00 ........?....... 00000020: 0000 0000 8000 8000 00f0 0a00 0000 0000 ................ 00000030: aa74 0000 0000 0000 0200 0000 0000 0000 .t..............
And on running file on the fixed dump, then it showed all the attributes of the partition
rnehra@pc ~> file dump2_fixed dump2_fixed: DOS/MBR boot sector, code offset 0x52+2, OEM-ID "NTFS ", sectors/cluster 8, Media descriptor 0xf8, sectors/track 63, heads 255, hidden sectors 718848, dos < 4.0 BootSector (0x80), FAT (1Y bit by descriptor); NTFS, sectors/track 63, sectors 716800, $MFT start cluster 29866, $MFTMirror start cluster 2, bytes/RecordSegment 2^(-1*246), clusters/index block 1, serial number 040ae5d9dae5d8c72
Questions based on dump 2
Q5. What is the size of cluster in bytes?
4096. Multiplybytes_per_sector(0x200) andsectors_per_cluster(0x08)
Q6. At what offset from the starting of partition the MFT table resides?
0x74aa000
Q7. What is the name of fist file?
$SOCGEN. Visible in last lines of first sector of the partition
Q8. Which is the first non-system or non-Meta file in MFT entry?
MYDATA.TXT Look at the location of non-Meta file here.
This is a good but easy online hackathon which requires knowledge of boot sector, filesystems and bootloaders basics. So I recommend the organisers that they can increase the difficulty a bit but I give them full marks for choosing a topic that teaches more about the system which I use everyday.